From a corporate perspective, regulatory compliance policies help to avoid legal issues, reputational damage, and financial penalties. Regulations also protect human safety, customer privacy, and the environment.
However, regulations are also complex and demanding. This article will explain how regulatory compliance works. We will look at variations between industries. And we will explore the benefits of implementing a comprehensive compliance program.
Regulatory compliance definition
Regulatory compliance refers to the adherence to laws or guidelines that apply to an organization. Following regulations can require legal compliance. In that case, companies must follow laws passed by governments. However, regulatory compliance can also involve privately administered business frameworks and standards.
What is regulatory compliance policy?
Regulations are sets of rules that are created and enforced by a recognized authority. Some regulations are defined by law and administered by federal agencies. Others are managed by private organizations. All regulations set penalties for violations. And regulations apply in every industry sector.
A regulatory compliance policy is a document that states how an organization meets its regulatory requirements.
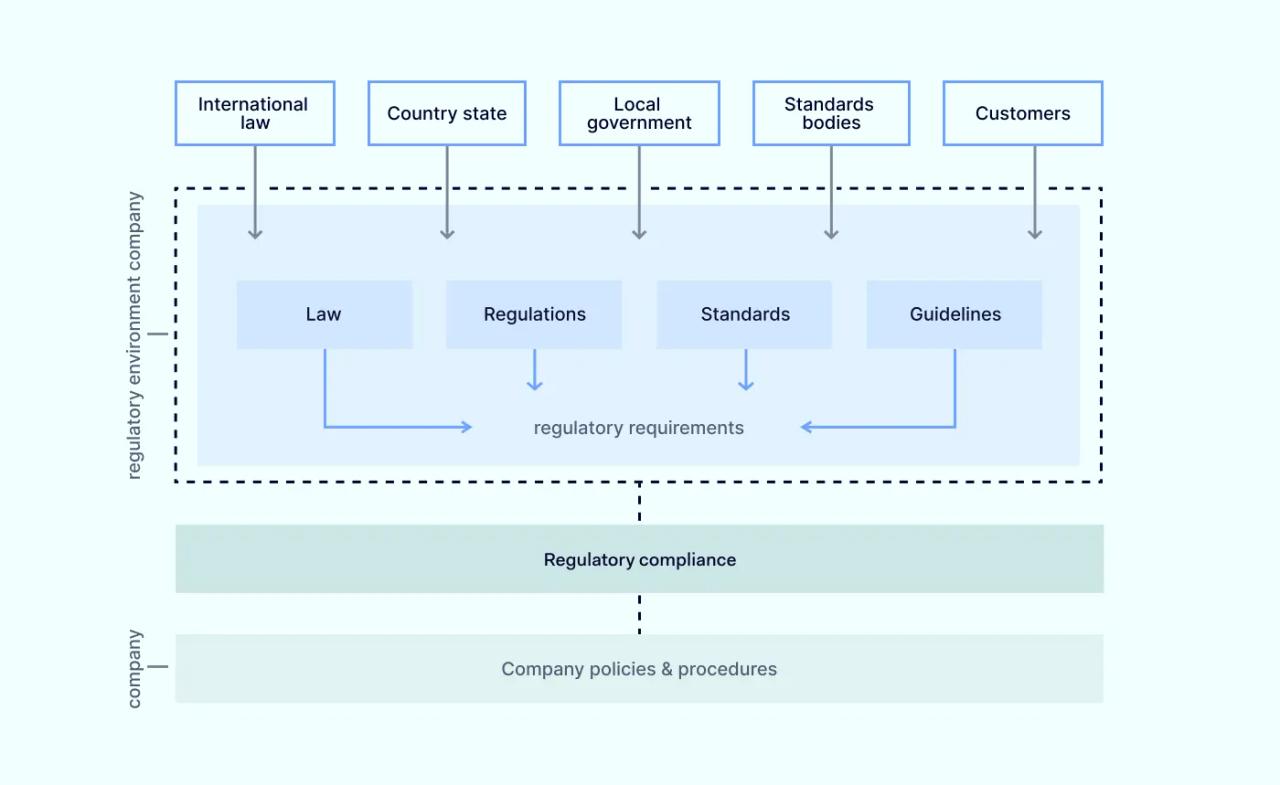
Compliance policies describe the rules, controls, and procedures used by the organization to meet its regulatory obligations. They show how the organization will ensure compliance in the future via audits and assessments.
Why is a regulatory compliance policy important?
Compliance policies play a critical role in ensuring that organizations meet their regulatory and information security obligations.
Strong compliance management reduces the risk of financial penalties. Regulatory compliance strengthens security systems. It builds trust with customers and partners. And it promotes enhanced data security within the organization.
A robust policy also ensures that companies can grow or expand into other jurisdictions without risking compliance breaches.
The increasing risk of cyber breaches
Robust regulatory compliance policies also help to minimize the risk of data breaches. The risk of cyber breaches is real and rising.
According to Checkpoint, weekly cyber attacks against companies rose 7% year-on-year from 2022 to 2023. The number of customer accounts affected by data breaches increased from 128 million in 2021 to 422 million in 2022.
Data protection regulations include detailed requirements to secure confidential data. Companies that follow these regulations will improve their security posture. They will make it harder for malicious actors to access customer data.
Regulatory compliance in key industries
Regulatory compliance varies between business sectors and geographical regions. Region-specific laws and frameworks may change the regulatory environment. Some sectors are more heavily regulated than others. For example, the actions required of health organizations differ from the responsibilities of e-commerce merchants.
Healthcare
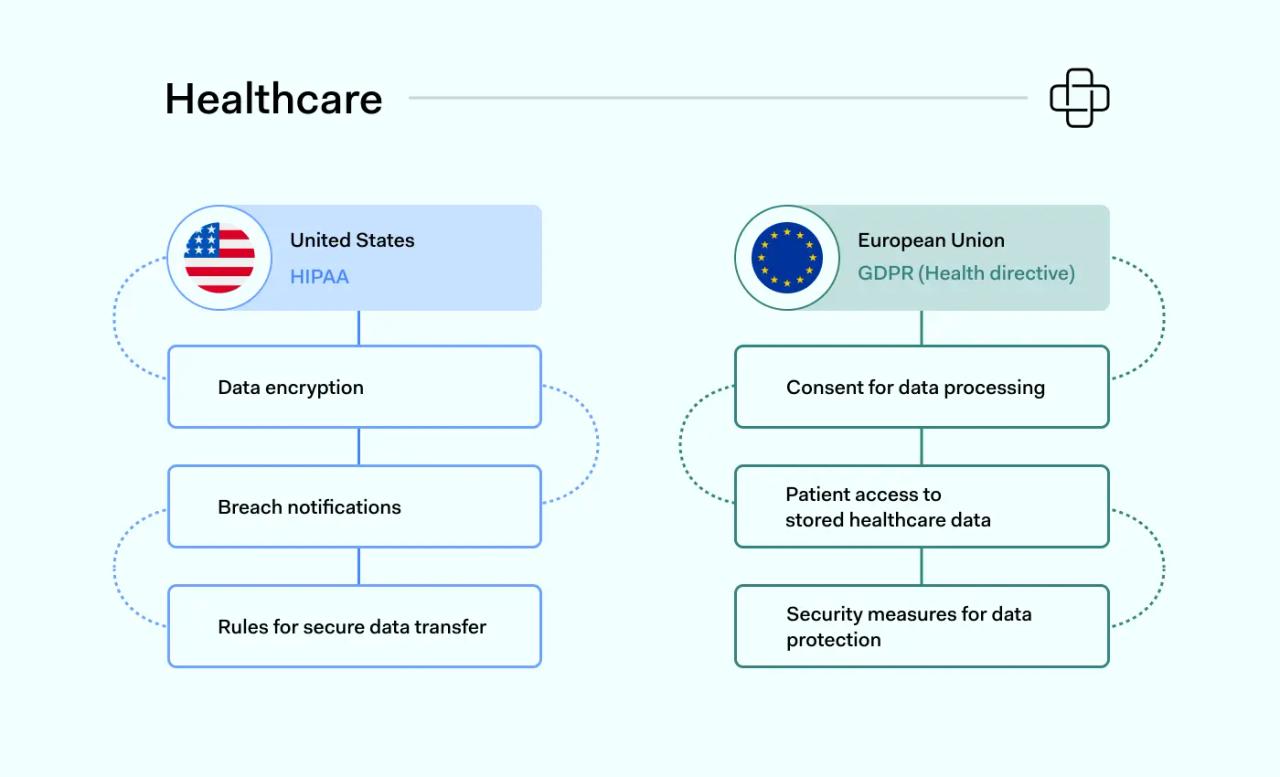
Healthcare organizations are tightly regulated because they handle private patient data. This type of data is extremely valuable for cyber attackers. Disclosure of personal health information can also lead to damaging privacy lawsuits.
United States
In the United States, the main healthcare regulation is the Health Insurance Portability and Accountability Act (HIPAA). HIPAA seeks to protect the privacy of health insurance policyholders. Key provisions include:
- Breach notifications when data is compromised
- Encrypting and protecting stored patient data
- Rules for transferring patient data securely
Security breaches are punished by fines and administered by the federal Office for Civil Rights (OCR). There are four violation tiers. Penalties are applied on a sliding scale. The size of the fine depends on:
- The scale of patient data exposure. This varies in terms of number of records and duration of exposure.
- Whether the organization involved could have prevented the data breach.
Individual states may enforce regulations of their own. For example, the California Consumer Privacy Act (CCPA) includes provisions to enhance patient privacy. Companies operating in California must make data available to patients. They must allow patients greater control over how their data is used.
The European Union
Healthcare companies operating across Europe are regulated by the eHealth Directive of the General Data Protection Regulation (GDPR). GDPR differs from HIPAA. It focuses on individual data privacy rights. Important provisions include:
- The need to secure explicit consent to store and process health data
- Patients must have access to stored healthcare data. Records should be deleted on request.
- Patient data should be secured by access controls, encryption, and regular security audits.
- Strict requirements when transferring health data outside the EU.
- Mandatory Data Protection Impact Assessments (DPIAs). DPIAs prove that organizations protect patient data.
GDPR has a global footprint and is not restricted to Europe. Companies can be fined a percentage of their worldwide turnover if they violate EU data privacy regulations.
There are two tiers of penalty. The maximum fine is either 20 million Euros or 4% of turnover. The size of the penalty is influenced by the severity of the offence. Mitigating factors may also reduce the size of GDPR fines.
Finance
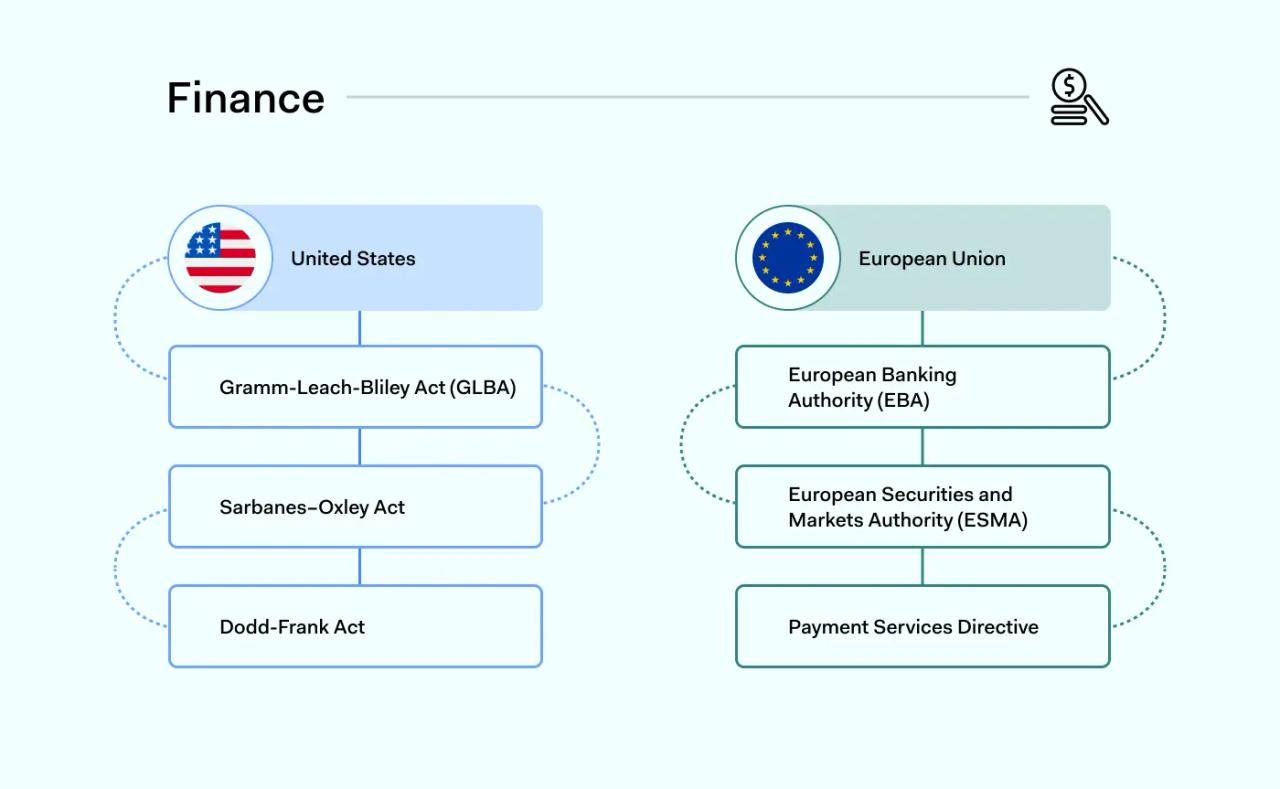
Financial companies are strictly regulated. Regulation prevents fraud and theft of personal financial information. As with healthcare, financial compliance differs slightly between the EU and USA. But both regions operate tight data security controls.
United States
Various regulations protect data security in the US financial sector. The most important federal regulation from a data security perspective is the Gramm-Leach-Bliley Act (GLBA). Also known as the Financial Modernization Act, GLBA requires companies to:
- Inform customers about how data is collected, stored, and used. Customers must be able to opt out of information sharing and affiliate marketing.
- Put in place safeguards to protect financial data. This includes risk assessments, security controls, and employee compliance training.
- Prohibit pretexting. This involves the collection of personal information under false pretenses.
In addition to GLBA, financial companies must comply with reporting requirements under the Sarbanes-Oxley Act (SOX). And they must obey consumer protections mandated by the Dodd-Frank Act. Neither is specifically related to information security. But both should figure in financial compliance policies.
The European Union
Financial companies in the European Union are regulated by the European Banking Authority (EBA) and the European Securities and Markets Authority (ESMA).
These agencies implement EU directives across the financial sector. For example, Payment Services Directive 2 (PSD2) sets out requirements for payment systems across the region. And the Markets in Financial Instruments Directive II regulates investment activity. There are regulations to combat money laundering. And specific rules regulate companies trading derivatives.
GDPR also regulates financial data security within the European Union. Regulatory compliance rules for financial companies are very similar to healthcare provisions.
Under GDPR, financial companies must:
- Allow customers to opt out of information sharing.
- Minimize data retention and provide a business case for retaining customer data.
- Process data securely with strong encryption
- Prevent unauthorized access.
- Execute regular security assessments.
- Inform customers of data breaches within 72 hours.
E-commerce
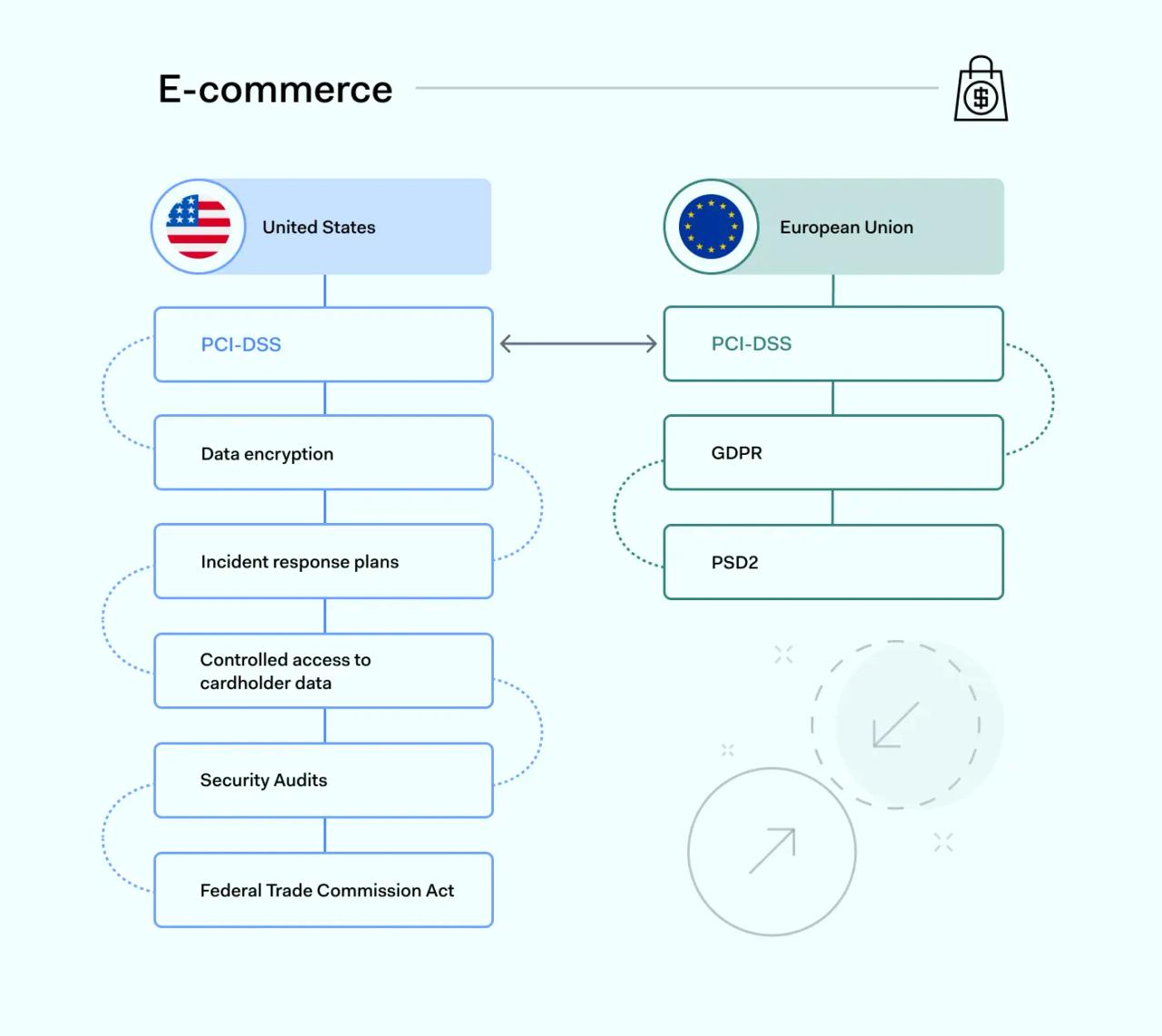
Credit card data breaches are the most high-profile regulatory compliance violations worldwide. And any organizations that store cardholder data must meet their legal obligations. As with other sectors, these obligations vary slightly between Europe and the United States.
United States
The most important regulations for digital merchants in the United States are the Payment Card Industry Data Security Standards (PCI-DSS).
PCI-DSS regulatory compliance is administered by the five main credit card companies (American Express, Visa, Mastercard, Discover, and JCB). PCI-DSS rules seek to protect credit card data by preventing fraud and data breaches. Typically, PCI-DSS-compliant organizations must:
- Encrypt data at rest and in transit
- Tightly control access to their cardholder data environment (CDE)
- Create incident response and recovery plans
- Regularly scan their systems and carry out security audits
PCI responsibilities vary depending on the size of the organization. Companies processing over 6 million annual transactions have greater regulatory compliance responsibilities than smaller businesses.
American e-commerce companies may need to comply with GLBA. Individual states operate data breach notification regulations. And they may launch prosecutions against violators. The Federal Trade Commission Act also provides the Federal Trade Commission (FTC) with powers to pursue companies that expose credit card data. So robust protection is advisable.
European Union
PCI-DSS rules apply to European Union companies that use the five main payment processors. Merchants must also comply with GDPR data privacy rules.
Under GDPR, credit card information is classified as protected personal data. Companies must apply safeguards to prevent data theft. Data privacy rules require consent to gather, process, or share cardholder data.
The EU's PSD2 directive also regulates card payments. PSD2 requires e-commerce companies to implement strong authentication processes.
Information technology
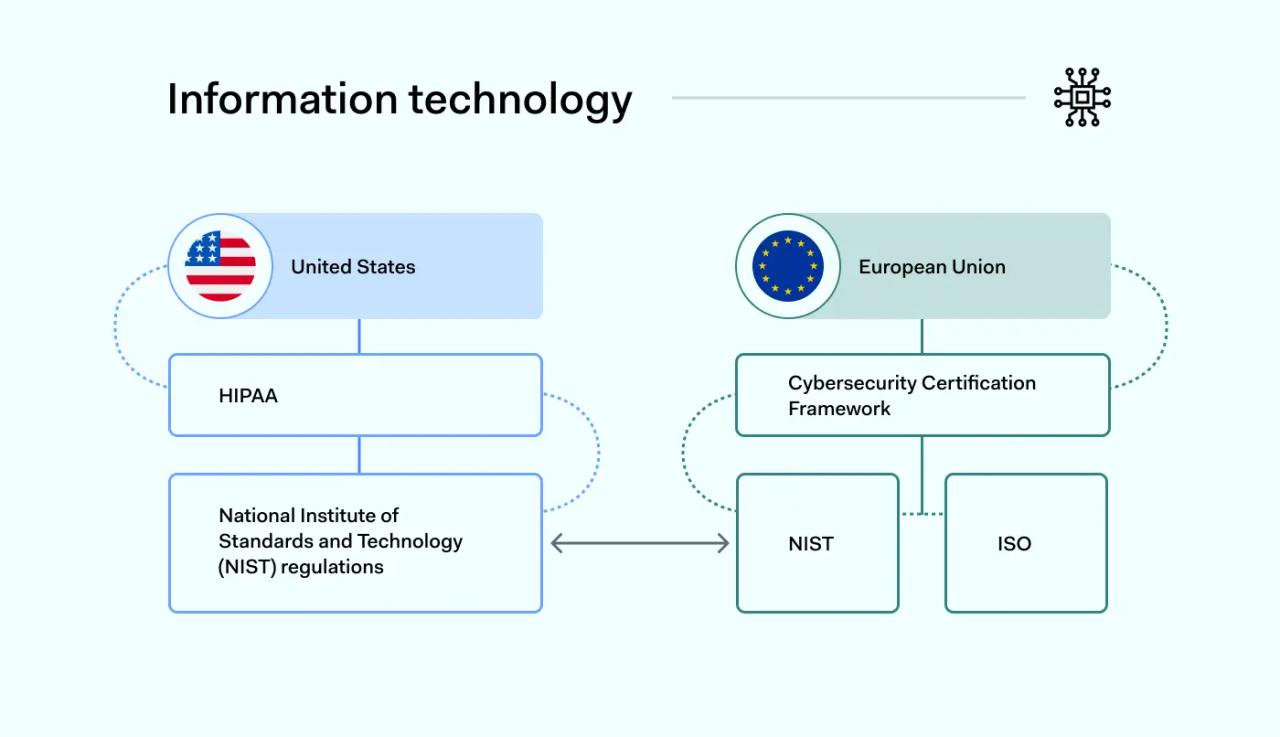
IT presents a different regulatory compliance picture. Data security and privacy regulations still apply. For example, IT companies that handle health data must comply with HIPAA. However, IT companies also base regulatory strategies on technical compliance standards.
Compliance standards provide information and guidance. But they can still be seen as regulations. This is because regulatory agencies use standards as a reference point to levy penalties.
United States
The main source of IT standards in the USA is the National Institute for Science and Technology (NIST). NIST is a federal agency that administers a library of compliance standards. These standards provide examples of IT best practices. They are regularly updated to reflect technological change.
The NIST SP 800 series is particularly important. This document series defines cybersecurity best practices for the IT sector. This includes important issues like conducting risk assessments and applying security controls. It also deals with handling security incidents.
NIST standards are not backed up by fines. But they are often referenced by regulators when levying penalties. Organizations that fail to comply with NIST SP 800 standards are also generally associated with poor data security.
European Union
Companies in the EU do not have access to an organization like NIST. However, the EU is planning to introduce a Cybersecurity Certification Framework. This framework will standardize cybersecurity best practices across the region.
IT organizations in Europe can use NIST standards as a compliance baseline. Many companies also rely on documents from the International Organization for Standardization (ISO). As with NIST, the ISO provides a set of best practices for specific IT challenges. ISO compliance helps to avoid GDPR compliance violations.
The benefits of remaining complaint
Regulatory compliance is more than a way to avoid prosecution or fines. Major benefits include:
- Trust and corporate reputation. Companies with a strong regulatory compliance record are seen as more trustworthy. Customers will be more likely to engage. They are more likelyto form lasting relationships. Partners will be keener to collaborate. The company's core message will be taken more seriously.
- Risk management. Regulatory compliance involves assessing risks and putting in place controls to mitigate these risks. Organizations can use compliance as an opportunity to understand their core risks. They can strengthen policies to protect their systems against external threats.
- Data breach protection and privacy. Companies that comply with GDPR or HIPAA must put in place strong customer privacy safeguards. This creates a robust environment where data is encrypted. Customer records are protected against unauthorized access. There is a lower risk of data breaches and regulatory violations.
- Efficiency. Regulatory compliance builds efficiency. Regulations force companies to analyze their operations. Organizations must reform inefficient network architecture. They must clean up user management systems that fail to protect critical data. Standardization simplifies corporate organization. This makes it easier to expand safely. It also streamlines internal workflows.
- Global operations. Companies operating globally require strong regulatory compliance departments. Merchants must comply with regulations in the EU and United States. They may also need to consider other jurisdictions. Without compliance expertise, global expansion is virtually impossible.
- Corporate culture and knowledge. Compliance management builds knowledge inside companies. Employees understand their security responsibilities. Knowledge about legal obligations makes workers more confident. And a robust compliance culture boosts morale. Employees want to work for respected, secure companies. They are unlikely to seek employment with organizations subject to repeated regulatory fines.
Building a strong compliance program
Compliance has many benefits and should be part of every organizational plan. But what does a compliance program look like? Compliance strategies generally follow a similar pattern. This flows from planning to assessment.
1. Appoint a Compliance Officer
Your Compliance Officer is responsible for overall compliance management. A competent Compliance Officer possesses deep knowledge of international regulations. They constantly monitor current regulatory compliance requirements.
Critical compliance management functions include:
- Carrying out risk assessments
- Establishing controls and recommending compliance technology
- Documenting compliance processes
- Auditing compliance strategies
- Training employees to meet regulatory obligations
- Reporting to regulators and senior managers
- Investigating violations and alerts
- Supporting whistle-blowers
2. Identify regulatory requirements
Building a compliance program involves understanding which regulations apply to the organization. Regulations vary between sectors. Companies operating in both the EU and the USA will need to consider multiple frameworks.
Remember that any companies taking payments from EU customers must comply with GDPR. And all companies taking credit card payments need a PCI-DSS compliance plan.
- Example: A company sells apparel in the United States and Europe. In this case, it must comply with FTC laws on competition and misleading claims. Its marketing must comply with the CAN-SPAM Act. Payment services must be PCI-compliant. And data handling for EU customers must meet GDPR standards.
3. Define your requirements under each regulation
Match up regulatory requirements with your business operations. Not all of the clauses of HIPAA or GLBA apply to each regulated entity. Carefully determine which requirements apply in your case.
Consider each relevant requirement in turn. Determine whether your organization currently meets that requirement. Assess whether additional controls are needed. Take action to mitigate any issues that violate compliance rules.
- Example: A US-based apparel merchant may need to update its data processing policies to comply with GDPR. They may add consent requests for sign-ups and transactions. And privacy notices may be needed for website visitors. Improved data encryption and access controls may be required for PCI-DSS and GDPR compliance.
4. Document your compliance strategy
Compliance policies define how the organization complies with regulatory requirements. Describe security controls in place for each requirement. Clearly explain how each control contributes to regulatory compliance.
Policies should also include a compliance code of conduct. This informs readers about their responsibilities in ensuring regulatory compliance.
Documentation should be written with compliance audits in mind. For example, documentation should make it easier to complete PCI-DSS self-assessment exercises. Policies should always be easy for auditors to understand and use.
5. Test and assess your compliance systems
Test security controls and ensure they perform their compliance function. If possible, bring in external experts to carry out a compliance policy review. This confirms that systems meet regulatory standards.
Compliance programs should always include regular assessment exercises. Regulations change all the time. Security controls and policies should also change when necessary. Compliance assessments ensure this happens.
Conclusion: understand your regulatory compliance needs
Regulations govern how companies act. They enforce strict penalties for non-compliance. Regulations vary between sectors. Companies must create compliance programs that suit their regulatory environment. This requires careful planning. Compliance programs also require skilled execution by compliance officers. Otherwise, companies risk fines, reputational damage, and prosecution.
