Zero Trust is a practical concept redefining an organization’s cybersecurity approach. Previously, the dominant mindset was — if the user has authenticated once, it should be considered trustworthy. Zero Trust challenges this stance, saying that modern cybersecurity requires stricter supervision at every access step.
Zero Trust Architecture is concerned with implementing real security systems aligning with the Zero Trust concept. We’ve outlined some good practices that can be applied when implementing Zero Trust security. They should expand endpoint visibility and enable greater control over the organization’s network.
Key takeaways
- Zero Trust is a modern approach to organizations’ cybersecurity
- Zero Trust should be a way to address specific cybersecurity issues in your company
- The first step of Zero Trust implementation would be to map your current perimeter
- Device identity should serve as one of the key components of a strong Zero Trust framework
- Monitoring should be centralized a be extensive enough to provide meaningful insights
- A local network shouldn’t be higher trust status based solely on its proximity
- Splitting your network into smaller units is one of the Zero Trust approaches and provides a better network control
- Verification methods can be combined to create more secure verification procedures
Zero Trust best practices
While cybercriminals constantly advance new hacking techniques, the same can’t always be said about most organizations’ IT assets. Obsolete firewalls, unpatched software, and legacy hardware are common examples of how poor internal management can threaten a company’s security.
Zero Trust is an approach to transform your organization’s cybersecurity and make it more resistant. When applied in Zero Trust Architecture (ZTA), it’s one of the most effective routes to increase a company’s cybersecurity status effectively. Here are some of the best practices for Zero Trust adoption that should help your transition.
1. Start with clear business objectives
You should first consider the actual business needs that could be improved by adopting more modern cybersecurity practices. Zero Trust as a mindset is beneficial to any business type, but it helps if you single out specific risks you need to resolve.
If your enterprise has already encountered cybersecurity accidents or some key areas of your business are exceptionally problematic, they should be your starting point. That way, your patching-up process will start from the areas that need the most attention, drastically improving your cybersecurity status.
2. Understand the protection surface
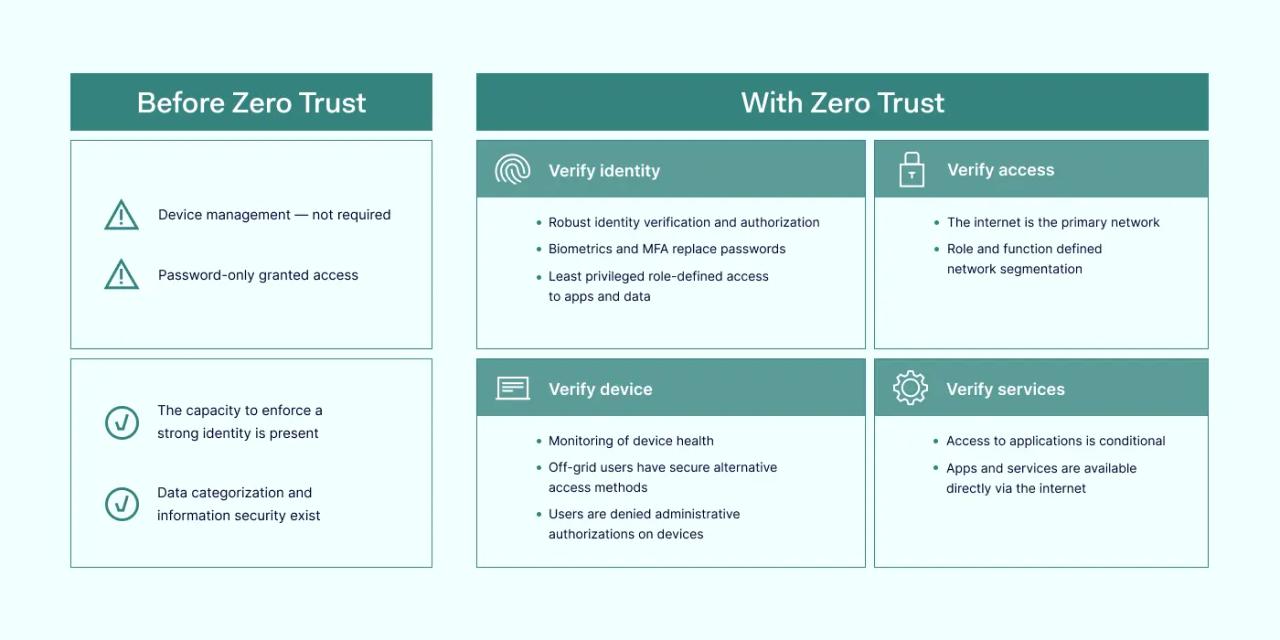
The Zero Trust approach will question your traditional perimeter security. As hackers are finding ways to breach the perimeter through already logged-on devices, the perimeter has largely been phased out as proof of security. Users’ network location shouldn’t be considered a factor when judging risk status.
Instead, the Zero Trust approach encourages looking into other ways to increase security without being tied to the perimeter. Some devices like IoT or printers can also serve as attack vectors. Various validation proof and mechanisms techniques should be developed to serve as a new basis for perimeter-less security.
3. Map out your network assets
Knowing the scope of your user base, used devices, and services will make your Zero Trust architecture building easier. A detailed overview of your network assets should shed light on what data needs to be made available and what risks it entails.
The riskiest assets will be those connected to the internet, as they could have some vulnerabilities that could be remotely exploited. You should narrow down your internet-connected assets and thoroughly evaluate them. While it’s true that legacy hardware and software might potentially have more security vulnerabilities, misconfigurations in modern hardware can do just as much damage.
4. Create a strong device identity
Device identity should serve as a strong and unique basis for authentication, authorization, and other security mechanisms. Rather than only focusing on user management, you should also make it possible to identify devices connecting to your network.
Additional elements could be introduced to help identify co-processors, software-based keys, and other solutions. Depending on the degree to which you can supervise the devices, it’s possible to provide a significantly high level of device authentication confidence.
5. Introduce centralized monitoring
No matter how many monitoring solutions you use, all the data should be accessible from a single dashboard to provide a holistic overview of the enterprise’s network. This prevents awkward cases when malicious activity is detected, but the report is missed or noticed too late.
Suspicious activity identification can be helped by various automation, as well. However, it’s important to note that each device should be evaluated based on the context. You should focus on ensuring that the analyzed traffic aligns with the security policies that you’ve set.
6. Don’t trust your local network
Adopting the Zero Trust framework means literally that — it extends to your internal network. This approach assumes that no channel is ultimately secure and requires strict authentication at each access step.
Trust can also be based on the devices and services used within your network. Even internal exchanges should also be done via secure protocols like TLS. This prevents a lot of cyberattacks that could be staged against your organization, including man-in-the-middle (MitM) attacks and DNS poisoning.
7. Segment your network
The Zero Trust approach will require you to split your network into smaller units. Segmentation of your total attack surface is intended to protect you in cases when your defense mechanisms fail, and the attacker infiltrates your perimeter.
You can use any combination of tools to help you out. One of the best ways would be to create a microcosm for your specific teams with a limited range of resources. The main idea is that only the data essential for providing main job functions should be available. This will prevent overexposure which could result in trouble when dealing with insider threats.
8. Combine multiple verification methods
User passwords are usually one of the weakest links in your organization’s cyber defense. They’re bought and sold in bulk in darknet marketplaces in the modern landscape. For this reason, you should make additional effort to secure this area. One of the best ways to do this is by requiring additional factor confirmations.
The more additional pieces of information you ask for, the harder it will be to bypass. Depending on your risk level, you can customize this requirement but avoid undergoing it. Multi-factor authentication should always be applied regardless of your users’ privilege levels. Don’t forget that you can request several additional factor confirmations for sensitive data types or network locations.
9. Implement Zero Trust policies
Your Zero Trust security policies should be based on your identified key risks. They should address your most critical areas by strengthening your weakest points. It’s also important to enforce these policies on all network workloads that your organization uses.
The easiest way would be to use various security tools to ensure that devices like IoT align with your company-wide security policies. Appropriate traffic flow should be ensured no matter the device used. This is a considerable cybersecurity risk; if left unchecked, this could leave an attack vector directly in your organization.
Zero Trust use cases
Here are some common use cases that drive organizations to implement Zero Trust. Remember that this list is not limited. Your Zero Trust policies could also help you with specific cybersecurity issues your company faces.
1. Reduce business and organizational risk
The Zero Trust approach puts the control of your organization’s cybersecurity back to you. The entrance to the network is denied unless the user passes authentication. In this framework, access is a privilege that is constantly rechecked and can be easily revoked.
This positively affects the network’s security as the security mechanisms are much stricter. The entry bar is raised, making it much harder to slip past it unnoticed. It also eliminates common cybersecurity problems like overprovisioned software and services that could serve as an attack vector.
2. Gain access control over cloud environments
One of the genuine concerns of IT administrators for cloud environments is less agency. The responsibility is shared between your organization and the cloud service provider (CSP). Still, CSP is fully responsible for server maintenance, and there’s a limit to how much you can affect their schedules and decisions.
Zero Trust can help alleviate some of the concerns associated with cloud networking. In this framework, security policies can be applied concerning the identity of communicating workloads. This ties company assets to security policies without relying on other network constructs. Protection always follows the workload no matter in what environment it’s in.
3. Reduce damage caused by data breaches
The assumption that every connection is hostile until proven otherwise can be invaluable when it turns out that’s the case. Inspecting each access request takes time, but it severely limits what a hacker can do once inside the network. Even if the hacker takes over someone else’s account, the trust is context-based, which can always be reassessed.
Without these checks, the network is left on its own, and hackers can freely roam your internal network. This makes data-stealing easier as there’s no internal segmentation to stop it. This approach restricts lateral movement capabilities, which is also tied to privilege escalation.
4. Supports compliance initiatives
Zero Trust can serve as a good basis for your cybersecurity revamp. It can be considered a future-proofing method if you’re trying to stay one step ahead of regulatory compliance requirements. The good practices required by Zero Trust will also align with PCI DSS or GDPR.
You can also get a much higher control of your network resources. During audits, this can serve as an example of what steps you are taking to protect your client’s data. This is much better visibility compared to traditional networks with overprivileged access.
5. Secure remote access
During hybrid work days, the enterprise network is greatly expanded. Remote employees and third parties are all participating when working together. Yet, it’s just as important to create controlled and safe access to the company’s internal assets.
Zero Trust sets organizations on the right track when ensuring that remote connections meet the safety requirements. The security policies outline how managed or unmanaged devices should be handled and what connections are secure to be initiated. They can still be reinforced with encryption, traffic monitoring, and other mandatory access checks. More about Secure Remote Access