Mandatory access control defined
Mandatory access control is a centralized access control system. MAC regulates access to resources based on the clearance levels of users and the attributes of objects they seek to access.
MAC is known for its high security levels. Organizations rely on it to protect sensitive data, limit the risk of cyberattacks, and meet regulatory requirements in fields like finance or healthcare. However, MAC does not prioritize flexibility. It's a centrally-managed, relatively rigid system. If flexibility is critical, discretionary systems may be preferable.
With mandatory controls, users can have different levels of authorization depending on their position and role. Admins can assign different sensitivity levels to data or applications, depending on security needs. Read on to learn about:
- How mandatory access control works
- The advantages of mandatory access controls
- Challenges associated with MAC
- Mandatory access control use cases
How does mandatory access control work?
Mandatory access control is a centrally-managed access system based on security labels. We call it "mandatory" because network users have very little freedom to share access or manage access permissions.
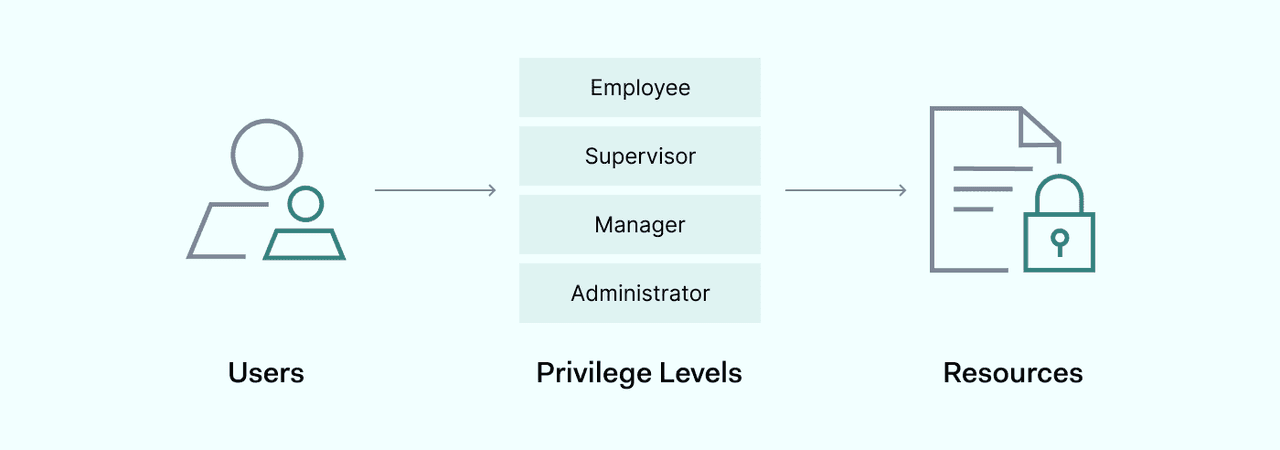
Administrators determine clearance levels and user groups from a central control panel. They do so by creating security labels for objects, and assigning privilege levels to network users.
A security label has two components: the clearance classification, and the security category.
Clearance levels
Mandatory access systems assign a clearance level to each user. This classification tells the operating system whether to grant access to sensitive data. Users must possess the clearance attributes associated with the object they seek to access. If not, access is denied.
Security categories
Administrators can also place objects in security categories. For example, classified data at security level 5 may be assigned to a specific project. In this case, users with level 5 clearance credentials can access the data. But they must also be members of the project. The system will deny access to level 5 users not assigned to the project.
The use of security labels gives MAC a degree of granularity. Administrators can create security groups and block unauthorized actors seeking access to data outside their role.
This is useful in situations where data security is critical. For instance, confidential, restricted, and top secret are common terms in government settings where secrecy is a priority.
Benefits of mandatory access control
Mandatory access control has strengths and weaknesses. And it suits some organizations better than others. Important benefits of mandatory based access control include:
Improved security and data protection
The system administrator can set access permissions for objects anywhere on the network. Users without the necessary clearance level cannot access these objects. There is also no scope to gain access by sharing credentials with others.
Preventing unauthorized access and limiting data breaches
Centrally controlled permissions limit the risk of data breaches. Attackers cannot exploit the many access points commonly found in discretionary access control systems.
Compliance with data protection standards
MAC is recommended by industry regulations like PCI-DSS. Companies handling financial data prefer mandatory controls to guard cardholder data environments or databases like insurance policyholders.
Clear visibility for system administrators
Centralized access controls make it easier to track who is connected to network assets. This can be a problem with discretionary setups, which can become hard to control at scale.
Challenges and limitations of mandatory access control
When choosing an access control system, security teams need to weigh up the pros and cons. Potential limitations of mandatory access control include:
Complexity and problems with implementation
Administrators can struggle to maintain MAC systems as user communities grow. Security teams must ensure permissions are up-to-date and reflect user roles. They must also onboard new hires and delete departing employees immediately.
The impact on user flexibility and productivity
Users must present their credentials whenever they seek to access data. This can be a major problem when using operating systems like Linux or Windows. Users cannot change their access settings. Only the system administrator can do so via the security kernel. Limiting access like this slows down data flows and can dent productivity.
Weak protection against insider threats
Mandatory access control protects against many attacks. But it is vulnerable to insider threats. Users with access to administrative privileges can bypass controls or grant access to outsiders. Clearance levels are not always enough protection to guard against insider threats.
Implementing mandatory access control
The implementation process for MAC varies but tends to follow a similar template.
- Central admins define security classifications and groups (such as projects or departments). This forms the basis for each security label.
- Administrators assign security attributes to each object. Each security label includes a clearance level and security category.
- Each user account is given security attributes appropriate for their role. This includes clearances and group memberships.
- When users access objects, the operating system compares their credentials to the MAC database. If they have the right attributes, the system grants access. If not, controls will deny access or request additional authentication information.
When organizations implement mandatory access control, it is essential to follow security best practices. Improper configuration can compromise clearance levels and role assignment. And it can slow down access systems, making networks harder to use.
Best practices to consider
Creating clear, relevant security labels
Labels should state the necessary clearance level. But it's also important to include security categories that locate the resource in the access system. Define user groups or roles clearly. Check that the right users have been assigned to the right groups.
Choose the right classification system
MAC systems involve clearance hierarchies with different classifications for users and objects. For example, documents might be classed as "public", "confidential," "secret", or "top secret.". Group users who share the same clearance level. And take care to assign objects with the right classification.
Explain how the system works
Clearance hierarchies should make sense to network users. Terms that make sense in military or intelligence organizations probably don't apply to credit card companies. Explain what each term means in security policies that are available to all users.
Test access systems
Do not assume that security labels automatically correspond to smooth access control. Make sure users without the required clearance levels are denied access. And ensure legitimate users can access resources easily without excessive interference.
Examples of mandatory access control in practice
Mandatory access controls are useful in multilevel security systems. They perform well in hierarchical environments. These settings involve tiers of different users, who have different security clearances.
This contrasts with multilateral security systems that apply rule sets across the same clearance level. Multilateral solutions such as discretionary access control work well in situations where speed and ease of use matter most. But they are less effective in guaranteeing data security.
MAC is quite rare in small business settings or consumer applications. But it does have some important use cases:
- Government, military, and intelligence agencies — these organizations use mandatory controls to enforce strict clearance tiers. Government bodies manage large quantities of secret data that require protection. But it must also be accessible to employees. MAC makes this possible. Administrators can set classifications and safely connect users with the confidential data they need.
- Businesses and other private organizations — large companies and organizations use MAC to guard customer data. For example, MAC allows insurance and banking companies to limit the number of users with access to financial information. This reduces the risk of data breaches and reputational damage.
Hybrid mandatory and discretionary access systems are common. For example, a company may enforce MAC via the Linux security kernel for accessing sensitive resources. But users can navigate the rest of the network with easy-to-use discretionary controls.
Mandatory access control is a centrally-managed access system. MAC assigns each network user a security level. It also assigns objects on the network with security attributes such as clearance levels and group identities. Users with the right security credentials can access protected objects. If not, access is denied.
MAC is secure and reliable. This makes it a common tool in high-security environments. But it creates administrative burdens, is not user-friendly, and can be difficult to operate at scale.
